Cloud Hosting Services
From planning, migration and deployment to ongoing management and optimization, NLT provides managed hosting services that quickly deliver ready-to-use cloud infrastructure and applications along with all the support needed to ensure high availability, performance, and security for you to meet your mission.
Cloud Hosting Services
From planning, migration and deployment to ongoing management and optimization, NLT provides managed hosting services that quickly deliver ready-to-use cloud infrastructure and applications along with all the support needed to ensure high availability, performance, and security for you to meet your mission.
NLT provides secure, private cloud options tailored to the demanding security requirements of US government agencies and other customers with highly sensitive data.
SECURE CLOUD HOSTING
Our secure cloud hosting for critical applications provides industry-leading automated security enforcement and continuous monitoring backed by our world-class support. With flexible options for government and commercial AWS, Azure, and Google clouds, single and multi-tenant compute configurations, high performance architectures, and other features, NLT hosting enables you to tailor your service so you never pay for something you don't want or need.
DATA SCIENCE SPECIALTY
NLT offers cost-effective, flexible service plans for turnkey managed hosting of leading Data Science, Geospatial, Remote Sensing & Imagery Exploitation Platforms optimized for serving a variety of big data, statistical computing, and Earth science missions.project.
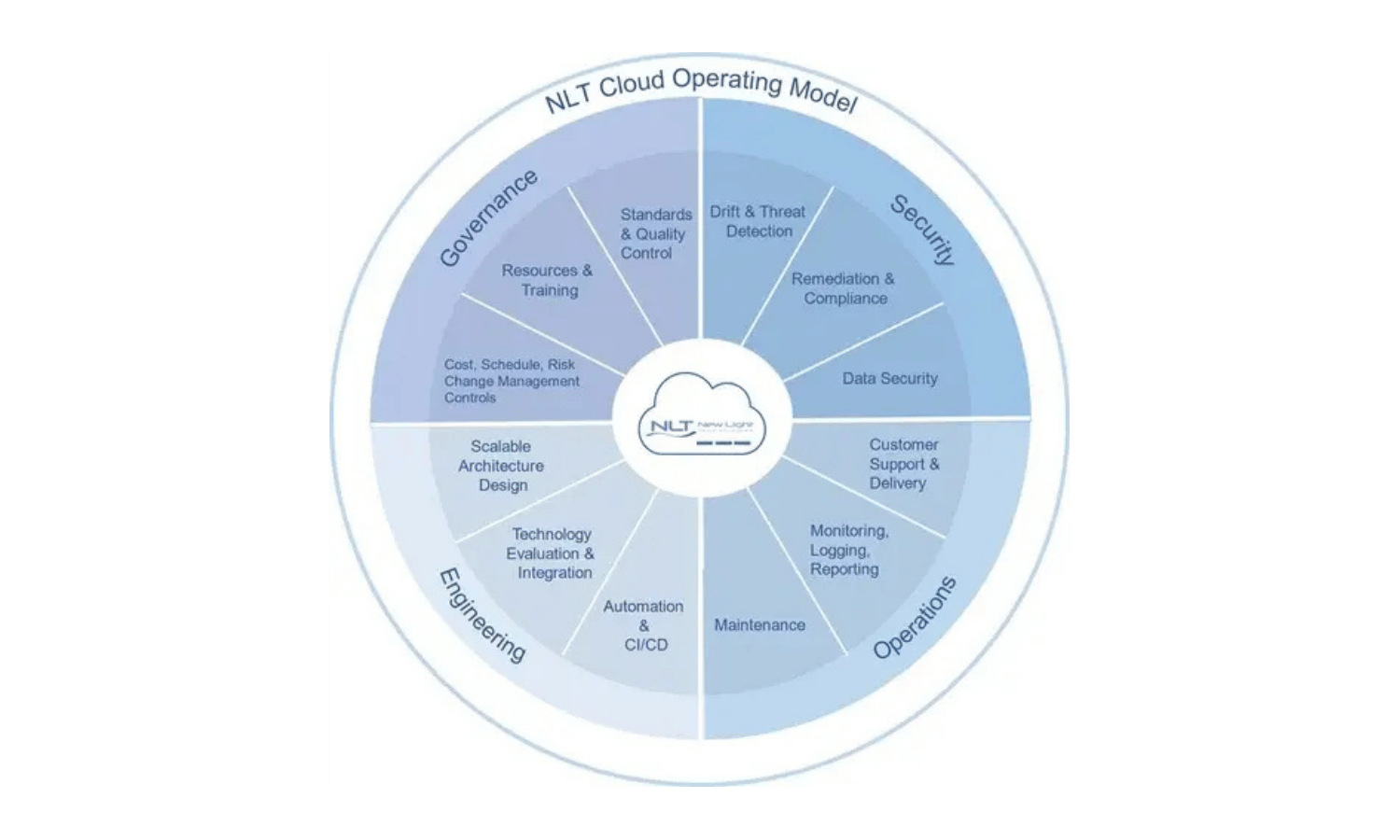
CLOUD OPPERATING MODEL
Over the course of our history building and managing diverse environments, we have developed a robust cloud practice, center of excellence, and Cloud Operating Model (COM) that guides our consulting and managed hosting services. Our model incorporates this experience and best practices for cloud engineering, security, operations, and governance to ensure the highest level of performance and satisfaction for customers.
NLT Hosted Features
Rapid Deployment
Our innovative infrastructure as code practices provide rapid deployment services to get you up and running quickly
High Performance
Our innovative infrastructure as code practices provide rapid deployment services to get you up and running quickly
Secure
Deploy to fully dedicated single-tenant compute infrastructure with NLT’s Automated Infrastructure Compliance Framework (AICF)
Scalable
Automatically scale to meet different demand requirements, mission use cases, and budgets
Customer Support
Continuous updates, monitoring, reporting, backup and recovery, and world class expertise & customer support
EXAMPLES OF OUR WORK
Geo4Dev is a cloud-native open-source platform for search & discovery of geospatial data for international development.
Book a Discovery Call
Contact us today to discover how we can uniquely tailor our services to meet the needs of your organization.
Explore some of our resources by our team of experts.
Cloud & Cybersecurity Automation
Whether migrating and managing legacy enterprise environments or building for the first time, our comprehensive Infrastructure-as-Code (IaC) solutions can help you get up and running quickly, securely, and scale with ease over time.
Our automated deployment and configuration tools ensure implementations are fast, testable, repeatable, self-documenting, and self-healing, CI/CD ready, and multi-cloud compatible.
NLT’s pioneering Automated Infrastructure Compliance Framework (AICF) provides state-of-the-art cybersecurity policy-as-code tools for any local or cloud computing environment. AICF provides:
Integrated pipeline for deploying and monitoring infrastructure
Pre-deployment policy checking using Open Policy Agent (OPA)
Post-deployment automated drift detection and remediation
Fully customizable easy-to-use deployable framework for cloud engineers




SITUATION
For years, Logoipsum manually tracked marketing metrics using Excel, Google sheets, and complex macros
SOLUTION
Logoipsum partnered with T2D3 to document their entire customer journey and map metrics at each stage
IMPACT
Logoipsum increased data accuracy by 76% and decreased manual data collection time by 4 hours per week

SITUATION
For days, HubSpot manually tracked marketing metrics using Excel, Google sheets, and complex macros
SOLUTION
Logoipsum partnered with T2D3 to document their entire customer journey and map metrics at each stage
IMPACT
Logoipsum increased data accuracy by 76% and decreased manual data collection time by 4 hours per week

Research
We provide a full range of services to lead, conduct & support research projects for complex science & technology challenges.

Data Science & AI
We offer unrivaled expertise managing full lifecycle development processes for large scale data production and visualization initiatives for government, non-profits, and industry.

Cloud & Managed Services
We offer extensive experience and a full suite of services in design, development, securing, deployment, and managing complex cloud and on-prem computing environments.

Cybersecurity
NLT’s synoptic integrated approach to cybersecurity can help you better understand, prepare for, and successfully defend against today’s cybersecurity threats.